Best Practices for Storing and Encrypting Passwords in WordPress
In the modern era of digital technology, it is of the utmost importance to protect user data, particularly passwords, in order to preserve trust, fulfil compliance requirements, and safeguard against cyber threats.
WordPress, the most popular content management system (CMS) in the world, offers powerful tools and functionalities for the safe saving of passwords.
However, to ensure the safety of sensitive information, it is necessary for site administrators and developers to go beyond the fundamental necessities. Within the scope of this piece, we will discuss the most effective methods for safely storing and encrypting passwords in WordPress. These approaches include hashing techniques and database security recommendations.

Become familiar with the way in which WordPress interacts with passwords
By default, WordPress uses the PHPass (Portable PHP password hashing framework) to hash passwords. PHPass uses a salted MD5-based hashing method, which was considered secure when it was first adopted. Although secure, this algorithm lacks some of the modern strength and adaptability found in more advanced algorithms like bcrypt and Argon2.
With PHPass, each password is hashed and salted, so even if an attacker accesses the database, cracking the hashes is challenging. However, some administrators may want to use newer hashing methods for enhanced security, especially for high-traffic or sensitive sites.
Despite this, it is a good idea to be educated about new and developing encryption technologies, as well as industry best practices, in order to guarantee the highest possible level of security. Security standards are constantly evolving.
Why does WordPress still rely on MD5?
In the past, it was difficult to incorporate a robust hashing algorithm into a PHP code. This began to change with PHP 5.5, released in June 2013, which included native support for bcrypt and functions for hashing and checking passwords during login attempts.
Currently, WordPress’s hashing technique provides sufficient security, but many feel that it is out of date, especially considering the availability of more resilient algorithms that might be easily applied.
Nonetheless, WordPress’s development team appears hesitant to change this key component, citing backward compatibility problems as the primary reason.
WordPress’s continued success stems from not only its variety and ease of use, but also its ability to run on nearly any hosting platform. Many users continue to create new projects using old systems, while countless existing sites are hosted on outdated platforms.
These out-of-date arrangements leave projects exposed to attackers, thus WordPress’s hashing process may be less of a concern. The developers understand that changing the hashing algorithm could have a wide-ranging impact, hence they choose to keep it unchanged.
This approach represents a “if it’s not broken, don’t fix it” mentality, which is understandable given the potentially vast number of individuals involved.
Make use of salts and keys that are both powerful and rare.
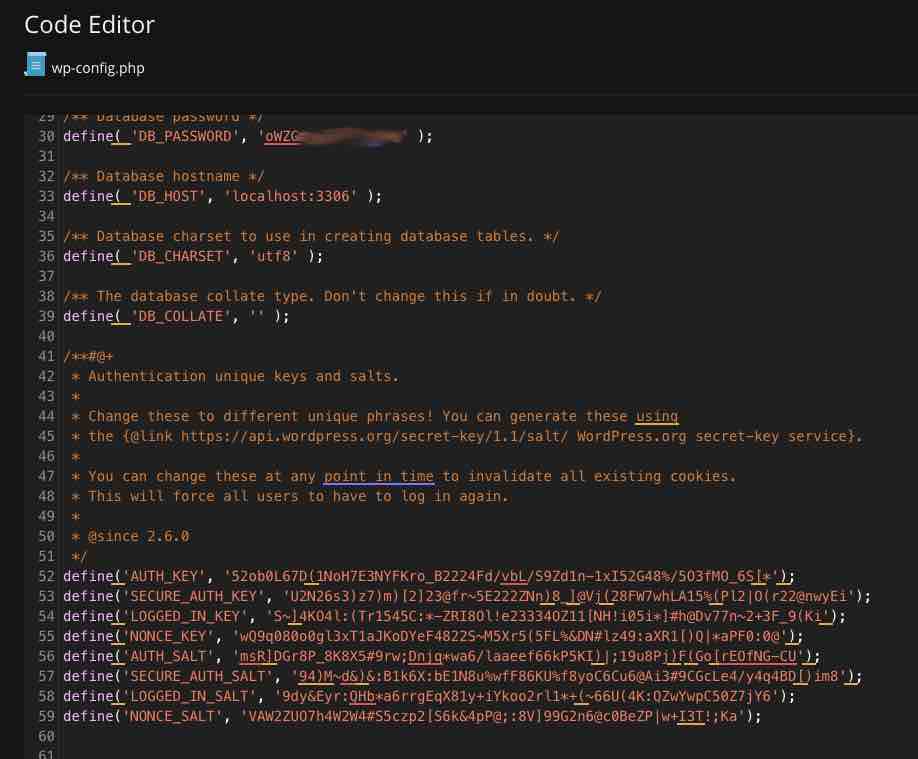
Both salts and security keys are necessary components for the encryption of passwords. The addition of these random strings gives the hashing process an additional layer of complexity, which makes it extremely difficult for adversaries to reverse-engineer passwords that have been hashed. WordPress is capable of automatically generating these salts; nevertheless, it is recommended that you update them on a regular basis:
The security keys should be updated. WordPress employs a collection of keys and salts within the `wp-config.php` file, namely under the `AUTH_KEY`, `SECURE_AUTH_KEY`, `LOGGED_IN_KEY`, and `NONCE_KEY` sections. By changing these keys regularly, you can assist maintain the integrity of the encryption. A fresh set of keys can be generated with the help of our WordPress’s Secret Key Generator (New API Salt Keys for WordPress), which provides an additional layer of protection.
There is a unique prefix for the database table. Make sure that the database prefix is always changed from the default `wp_` to something that is unique whenever you are installing WordPress. Because of this, it is more difficult for attackers to guess the names of the tables and gain access to sensitive data.
Keep in mind that you should never store plain text passwords.
Simple passwords pose a significant threat to the security of a system. It is imperative that you never keep passwords in a format that may be read by your computer. Not only does this constitute a violation of the regulations governing the protection of personal data, but it also puts user accounts open to attack in the event that the database is breached.
While WordPress does its best to hash passwords, it is important to remember that you should always hash passwords before saving them if you are developing custom login or registration forms. Make sure that user passwords are encrypted correctly by utilizing the `wp_hash_password()` function. One of the best and fastest WordPress Password Hash Generator is HashifyWP.
Use a robust hashing algorithm that has a high-cost factor. This is the fourth recommendation.
The bcrypt method that is already installed on WordPress is a safe option; but, if you are dealing with really sensitive data or if you want to add an additional layer of safety, you might think about using more complex hashing choices. Among the suggestions are the following:
Adjusting the Cost Factor: Bcrypt gives you the ability to change the cost factor, which has an effect on the amount of time needed to compute the hash. A greater cost factor results in improved security, but it necessitates a greater amount of computing power.
Consider Argon2: Argon2 is yet another contemporary hashing algorithm specially intended for the protection of passwords. Although it is more secure and adaptable than bcrypt, integrating it in WordPress takes a greater level of modification than bcrypt does.
When working with custom hashing algorithms, it is important to ensure that they are compatible with the resources of your server and that users do not encounter any delays when they are obtaining their login credentials.
Make sure that all user communications are encrypted before sending them.
When it comes to ensuring the safety of data transmissions, SSL (Secure Sockets Layer) is absolutely necessary. SSL encrypts the data that users enter when they log in or enter sensitive information, prevents it from being intercepted by bad actors, and gives users peace of mind. When SSL is enabled:
It is recommended that you get and set up an SSL certificate for your domain.
Please update the settings of WordPress so that HTTPS is used for all URLs. In order to guarantee the safety of all users, redirect HTTP traffic to HTTP Security.
An SSL certificate is essential for ensuring the safety of connections between the devices used by users and your server, particularly for pages that need users to log in or register.
Limit access to sensitive database fields, as stated in the sixth point.
Hashing passwords is a method of protecting them while they are being stored; nevertheless, controlling access to the database is also very significant. Having unauthorized access to the tables in your database could result in the disclosure of additional information or the extraction of passwords that have been hashed. Your database can be protected by:
When it comes to restricting database user access, you should only grant the bare minimum of permissions that are necessary for database users. The likelihood of illegal access and inadvertent data disclosure is decreased as a result of this.
The process of regularly updating user permissions involves reviewing and updating access permissions for users on a regular basis. This ensures that only those users who require access to sensitive data are granted access to those tables.
Put in place two-factor authentication and account lockouts
Improved security can be achieved through the use of two-factor authentication (2FA) and account lockouts in the event that unsuccessful login attempts are made. Even if an adversary is successful in guessing or stealing a user’s password, those additional layers make it substantially more difficult for them to get access to accounts.
The following plugins are recommended for use with two-factor authentication and lockouts: – Two-Factor Authentication: This plugin enables a number of two-factor authentication methods, such as email, TOTP apps, and FIDO U2F.
It prevents brute-force attacks by restricting the number of login attempts that can be made from a single IP address. – “Limit Login Attempts Reloaded”
By integrating 2FA and account lockouts, you add multiple barriers that prevent unauthorized access, even in the event of a compromised password.
Regularly Audit and Update Security Practices
The procedures of encrypting data and passwords are continually moving forward. Regular security audits should be performed on your WordPress website in order to uncover security flaws, underused themes, and plugins that have become obsolete. Take the necessary steps to ensure that all of your security plugins, core WordPress files, and server software are up-to-date.
Periodic audits allow you to assess the effectiveness of your encryption and hashing methods, ensuring you stay ahead of potential vulnerabilities.
Giving User Security the Highest Priority Through Strengthening Encryption
Protecting user passwords isn’t just about meeting regulatory requirements; it’s about fostering trust and safeguarding your website’s integrity. By following these best practices, you protect your users and build a strong, secure environment for them to interact with your WordPress site. For further security, consider working with security experts who can assess your setup and make recommendations tailored to your specific needs.
Securing passwords in WordPress is a multi-layered approach that requires attention to detail, regular updates, and a commitment to staying informed. Let’s keep the users safe, one hashed password at a time!